In the world of cybersecurity, there are many tools available on the internet, many of them are free and others are paid. we are quite sure that people around the world are utilizing these tools to infamous themselves in various aspects but the word hacking also considers the terms of illegal which means without the prior permission of the representative, so by doing this you could face law enforcement. Also Read: How To Secure Your Android From Hackers
List of 25 Most Popular Hacking Tools For Hackers in 2021
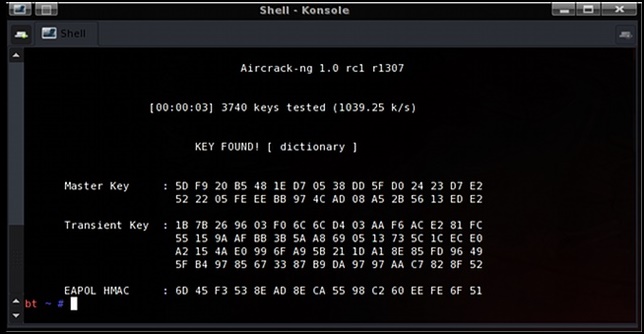
1. Aircrack-ng
Aircrack-ng.org is an 802.11 WEP and WPA-PSK keys breaking program that can resolve keys once enough information regarding the term stolen. It executes the standard FMS attack alongside a few improvements like the KoreK breach and additionally the all-new PTW attack, in this way making the assault much quicker contrasted with other WEP splitting devices. Actually, Aircrack-ng is an arrangement of software for evaluating remote systems.
2. sqlmap
sqlmap is an open-source infiltration testing device that robotized the procedure of recognizing and abusing SQL infusion imperfections and assuming control of database servers. Full support for MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, and HSQLDB database management systems. It accompanies an effective identification program, numerous corner elements for a definitive infiltration analyzer, and an expansive scope of changes enduring from database fingerprinting, over information getting from the database to getting to the basic record framework and executing orders on the working framework through an out-of-band network.
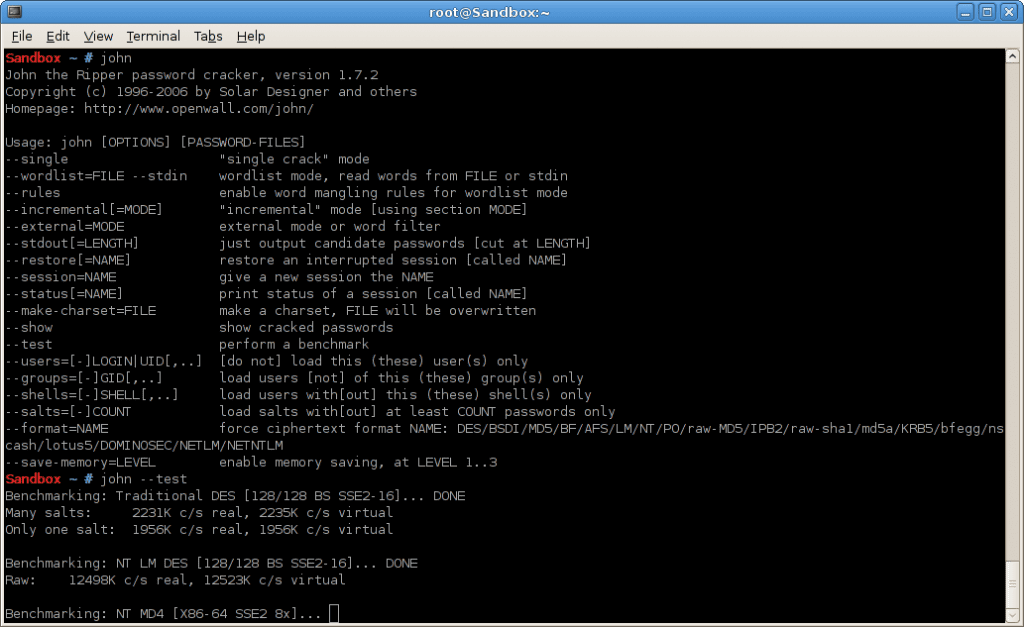
3. John The Ripper
John the Ripper is a free secret password cracking tool. At first, it was created for the Unix working framework, it now keeps running on fifteen distinct stages (eleven of which are building design particular adaptations of Unix, DOS, Win32, BeOS, and OpenVMS). It is a standout amongst the most mainstream watchword testing and breaking projects as it joins various secret word wafers into one bundle, autodetects watchword hash sorts, and incorporates an adjustable. It can be kept running against different scrambled secret word organizations including a few sepulcher watchword hash sorts most usually found on different Unix variants (in view of DES, MD5, or Blowfish), Kerberos AFS, and Windows NT/2000/XP/2003 LM hash. Extra modules have extended its capacity to incorporate MD4-based secret key hashes and passwords put away in LDAP, MySQL, and others.
4. Nmap – Network Mapper
Nmap is a contraction of ‘System Mapper’, just like an exceptionally surely understood free open-source programmers device. Nmap is utilized for system disclosure and security examination. Numerous framework administrators use Nmap for system stock, open ports, overseeing administration update timetables, and observing host or administration uptime. The apparatus utilizes crude IP parcels as a part of innovative approaches to figure out what hosts are accessible on the system, what administrations (application name and form) those hosts are putting forth, what working frameworks (and OS renditions and conceivable patches), and what sort and form of bundle channels/firewalls are being utilized by the objective. Nmap keeps running on all real PC working frameworks, and authority parallel bundles are accessible for Linux, Windows, and Mac OS X. Notwithstanding the fantastic charge line Nmap executable, the Nmap suite incorporates a propelled GUI and results from the viewer, an adaptable information exchange, redirection, and investigating apparatus, a utility for looking at output results, and a bundle era and reaction examination device.
5. THC Hydra
THC Hydra is another exemplary watchword splitting apparatus. Entirely speaking Hydra is a system login watchword splitting apparatus, which is very quick. An extraordinary element about Hydra is that you can add modules to expand the usefulness of this hacking instrument. When you have to savage power break a remote association administration, Hydra is regularly the instrument of a decision. It can perform fast word reference assaults against more than 50 conventions, including telnet, FTP, HTTP, https, smb, a few databases, and considerably more. Like THC Amap this discharge is from the fine people at THC. Other online wafers are Medusa and Ncrack. The Nmap Security Scanner additionally contains numerous online savage power secret key splitting modules.
6. Burp Suite
Burp Suite is an incorporated stage that was fabricated to assault (pentest) web applications. The stage contains many hacking devices with various GUI interfaces that encourage and accelerate the procedure of assaulting an application. As ever, the apparatus is intended to have a similar outlook as a dark cap programmer would. Burp Suite is a coordinated stage for performing security testing of web applications. Its different instruments work consistently together to bolster the whole testing procedure, from starting mapping and investigation of an application’s assault surface, through to discovering and misusing security vulnerabilities.
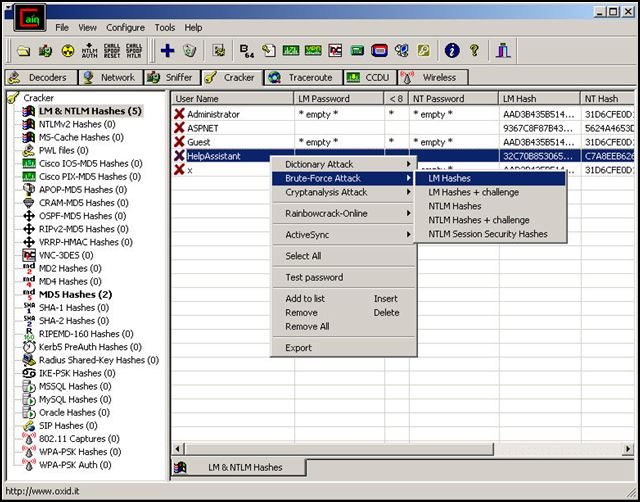
7. Cain and Abel
Cain and Abel (regularly abridged to Cain) are a secret key recuperation instrument for Microsoft Windows. It can recuperate numerous sorts of passwords utilizing techniques, for example, system parcel using so as to sniff, breaking different secret key hashes routines, for example, lexicon assaults, animal power, and cryptanalysis assaults. Cryptanalysis assaults are done by means of rainbow tables which can be created with the winrtgen.exe project gave Cain and Abel. Cain and Abel are kept up by Massimiliano Montoro and Sean Babcock. Recording VoIP discussions, translating mixed passwords, recuperating remote system keys, uncovering secret key boxes, revealing stored passwords, and breaking down steering conventions. The system does not misuse any product vulnerabilities or bugs that couldn’t be altered with little exertion. It covers some security viewpoints/shortcoming present in convention’s norms, verification routines, and reserving components; its primary design is the disentangled recuperation of passwords and qualifications from different sources, on the other hand, it likewise sends some “no standard” utilities for Microsoft Windows clients.
8. OWASP Zed
The OWASP Zed Attack Proxy (ZAP) is a simple to utilize integrated penetration testing tool for finding vulnerabilities in web applications. The Zed Attack Proxy (ZAP) is currently a standout amongst the most mainstream OWASP ventures. This hacking and a pentesting instrument is an exceptionally proficient and ‘simple to use’ program that discovers vulnerabilities in web applications. It is intended to be utilized by individuals with an extensive variety of security experience and as being what is indicated is perfect for designers and useful analyzers who are new to entrance testing. ZAP is a mainstream device on the grounds that it has a ton of bolster and the OWASP group is truly an astounding asset for those that work in Cyber Security. ZAP gives robotized scanners and an arrangement of instruments that permits you to discover security vulnerabilities physically.
9. Maltego
Maltego is a computerized legal sciences stage that was made to convey a digital danger picture to the earth in which an association works. The one of a kind viewpoint that Maltego offers to both system and asset-based substances is the accumulation of data posted everywhere throughout the web whether it’s the present arrangement of a switch balanced on the edge of your system or the present whereabouts of your Vice President on his global visits, Maltego can find, total and picture this data. Maltego is a one of a kind stage created to convey an unmistakable danger picture to the environment that an association possesses and works. Maltego’s interesting leeway is to exhibit the many-sided quality and seriousness of single purposes of disappointment and in addition trust connections that exist presently inside of the extent of your base.
10. Metasploit
Metasploit is a much more popular tool. Cybersecurity allows a penetration tester and hackers to use this tool, its function is to seek the security of the network by making a vulnerability along with the system also. What’s more, Metasploit likewise obliges productive administration and testing of Intrusion Detection Systems. The most well known “division” of this ‘multi-reason hacking device’ is the open-source Metasploit Framework Project, ordinarily alluded to as essentially ‘Metasploit’. This apparatus helps the client create and execute (known or generally) adventure code against a remote target machine. Numerous Metasploit clients utilize the apparatus for hostile to criminological and avoidance purposes, a large number of which are incorporated with the Metasploit Framework.
11. Wireshark
Wireshark is perhaps the best known ‘Programmers Tool’ out there. Wireshark has been around for quite a while now and it is utilized by a huge number of security experts to troubleshoot and break down systems. Wireshark is a fabulous programming and correspondences convention improvement and instruction. Initially named Ethereal, in May 2006 the task was renamed Wireshark because of trademark issues. It is free and open-source parcel analyzer.
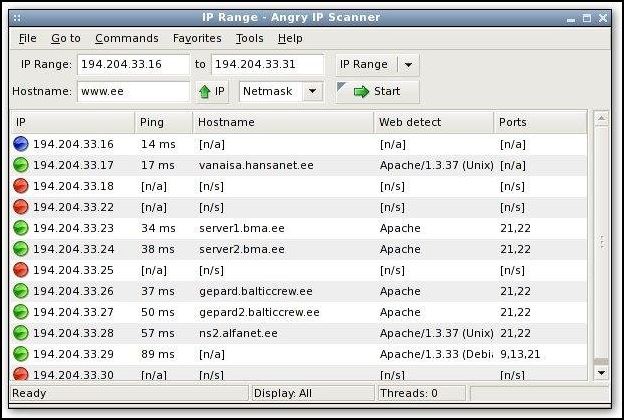
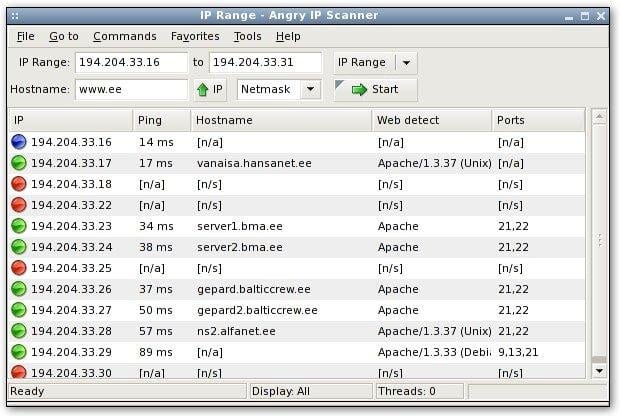
12. Angry IP Scanner
Angry IP Scanner on the other hand known as ipscan is an open-source and cross-stage system scanner intended to be quick and easy to utilize. It examines IP addresses and ports and has numerous different elements. It is generally utilized by system executives and simply inquisitive clients around the globe, including huge and little endeavors, banks, and government organizations. It keeps running on Linux, Windows, and Mac OS X, potentially supporting different stages too.
13. Nessus Remote Security Scanner
At the odd days previously this software tool is much more popular by the demand of the hacking world, currently, this application source is unavailable for official but users can still use it for free, it usually works with a client-server system, it helps users to find out vulnerability, it has been used by more than 75,000 companies. Nessus Security Scanner is the most famous for companies, Nessus helped many big companies to analyze their business proportional audit process which is efficient cost-saving.
14. Ettercap
Ettercap is a free and open-source system security device for man-in-the-center assaults on LAN. It can be utilized for PC system convention examination and security evaluating. It keeps running on different Unix-like working frameworks including Linux, Mac OS X, BSD, and Solaris and on Microsoft Windows. It is equipped with blocking movement on a system section, catching passwords, and leading dynamic listening stealthily against various normal conventions. Ettercap meets expectations by putting the system interface into a wanton mode and by ARP harming the objective machines. Along these lines, it can go about as a ‘man in the center’ and unleash different assaults on the casualties. Ettercap has a plugin bolster so that the elements can be stretched out by including new plugins.
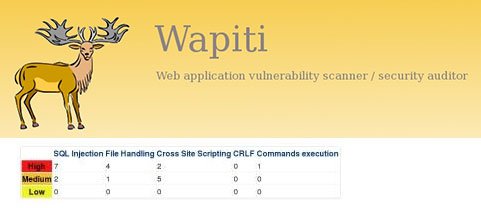
15. Wapiti
Wapiti is a web application vulnerability scanner tool allows you to audit the security of your web application through scanning the application and program of the web it works “black-box” types of scanning that will scan the webpages of the deployed web app but will not study the source code of the web pages and from the web page can scan it to inject data.
16. Nikto
Nikto Web Scanner is a Web server scanner that tests Web servers for dangerous files/CGIs, outdated server software, and other problems. It performs generic and server types of specific checks. It also captures and prints any cookies received. The Nikto code itself is Open Source (GPL), however, the data files it uses to drive the program are not.
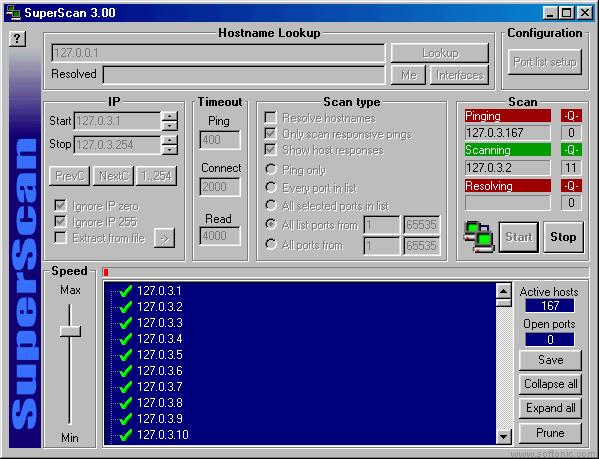
17. SuperScan
SuperScan is a Powerful TCP port scanner, pinger, resolver. You can get improved host detection using multiple ICMP methods, TCP SYN scanning. Moreover, you will get a selection of useful tools (ping, traceroute, Whois, etc)
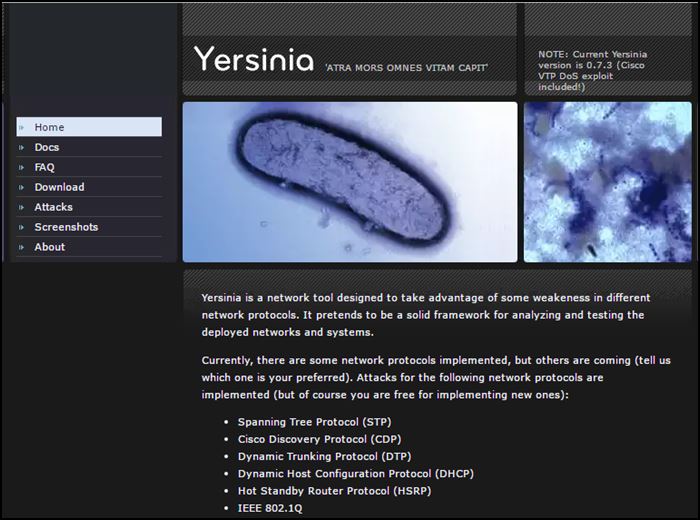
18. Yersinia
Yersinia is a network security/hacking tool for Unix-like operating systems, designed to take advantage of some weakness in different network protocols. Yersinia is considered a valuable and widely used security tool. It pretends to be a solid framework for analyzing and testing the deployed networks and systems.
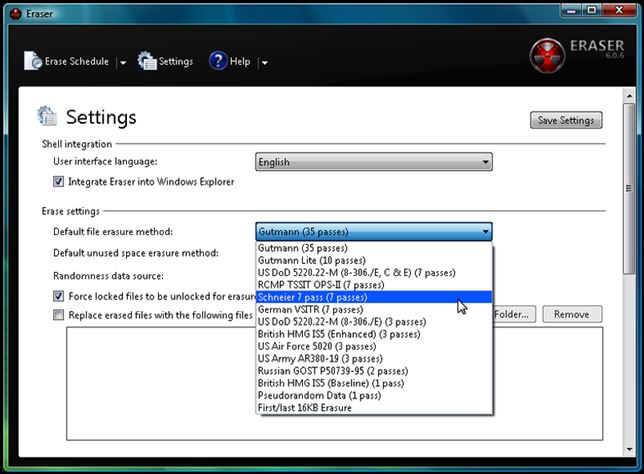
19. Eraser
Most people have some data that they would rather not share with others – passwords, personal information, classified documents from work, financial records, self-written poems, and the list continues. An eraser is a security tool for windows that simply allows users to remove sensitive data from their hard drive by overwriting several times with selected patterns.
20. Acunetix Vulnerability Scanner
Over 70% of websites and web applications contain vulnerabilities that could lead to data theft. Acunetix used to crawl your web page and automatically analyzes all your web apps and finds perilous SQL injection, Cross-site scripting, and other vulnerabilities that expose your online business.
21. Angry IP Scanner
This is one of the most used hacking tools for IP addresses and ports lookup. Angry IP Scanner is an open-source tool that provides researchers plenty of features to scan IP addresses and ports to look for doorways into a user’s system.
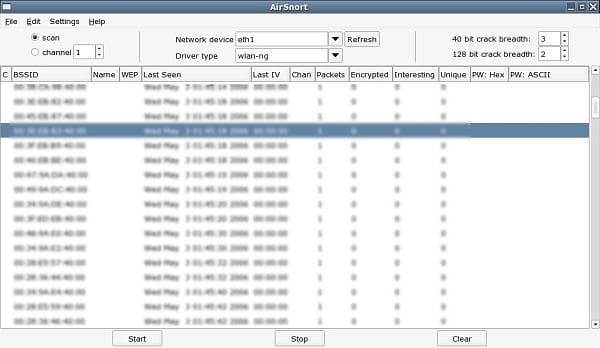
22. Airsnort
Airsnort is another best tool for wireless hacking. This is one of the popular tools which is used to decrypt the WEP encryption process. AirSnort is freely available and supports on Windows and Linux operating systems. This tool monitors transmissions and computing encryption keys once it has enough packets received.
23. Netsparker
This is another popular tool that is used by hackers in order to find flaws in web applications. The tool is powerful enough to find flaws like SQL injection and local file induction. The tool also provides remedies to help you recover from any kind of flaws.
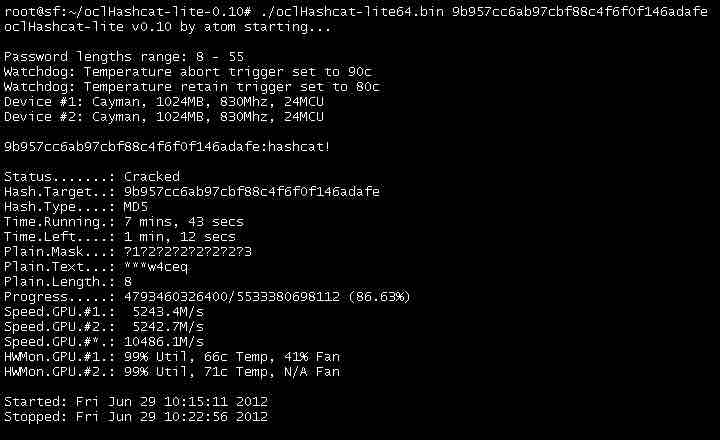
24. oclHashcat
Well, if you keep great interest in the password cracking tool, then oclHashcat is the best tool you can have. oclHashcat is a CPU-based password cracking tool and it comes with some advanced version that uses the power of your GPU. The tool calls itself the world’s fastest password cracking tool with the world’s first and only GPGPU based search engine.
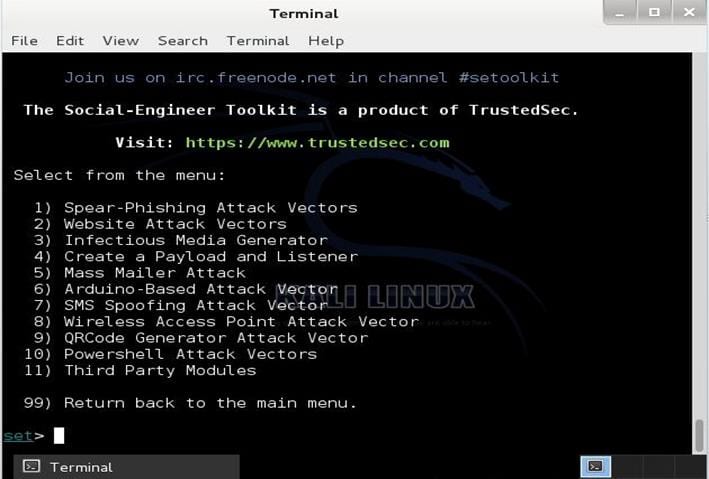
25. Social-Engineer Toolkit
Social-Engineer Toolkit also got featured on Mr.Robot TV series. This is an advanced framework for simulating multiple types of social engineering attacks like credential harvestings, phishing attacks, and more. Well, this is basically a Python-driven tool that is used for social engineering penetration tests with more than two million downloads. If you found any tool that we have missed, then you can comment on that in the comment box below. Hope you like the post, share it with your friends too.